In today’s connected world, applications rarely work in isolation. They need to securely access data and services from other systems — but without exposing sensitive credentials like usernames and passwords. This is where OAuth 2.0 comes in.
OAuth 2.0 is an open standard authorization framework that allows applications to access a user’s resources on their behalf without sharing the user’s credentials. Instead, OAuth uses tokens to grant access in a secure and controlled way.
When we bring PingFederate into the picture, it acts as the Authorization Server (AS) that manages token issuance, validation, and security policies for OAuth-based authentication and authorization.
Why OAuth 2.0 Matters
- Security – Users don’t have to share their passwords with every app or service.
- Granular Access – Access can be limited to specific resources or actions (using scopes).
- Better User Experience – Single sign-on and seamless app-to-app access.
- Industry Standard – Widely adopted and supported across platforms.
PingFederate’s Role in OAuth
PingFederate by Ping Identity is a centralized identity and access management solution that implements OAuth 2.0 at an enterprise level.
As an Authorization Server, PingFederate:
- Issues Access Tokens that allow applications to call APIs securely.
- Issues Refresh Tokens so clients can renew expired access without prompting the user.
- Supports multiple OAuth flows for different application types (web apps, mobile, APIs, SPAs).
- Provides OAuth endpoints like authorization, token, introspection, revocation, and metadata.
- Enforces security best practices like PKCE for public clients, scope management, and token validation.
Key OAuth Concepts in PingFederate
Before diving into configurations (which we’ll cover in separate articles), let’s understand the main building blocks of OAuth with PingFederate:
| Concept | Description |
|---|---|
| Resource Owner | The user or system that owns the protected resource. |
| Client | The application requesting access on behalf of the user. |
| Authorization Server (PingFederate) | Issues tokens after validating the request. |
| Resource Server | API or service that holds the protected data. |
| Access Token | A short-lived credential used to access resources. |
| Refresh Token | A longer-lived token used to get new access tokens without user re-login. |
| Scope | Defines the level of access being granted (e.g., read, write). |
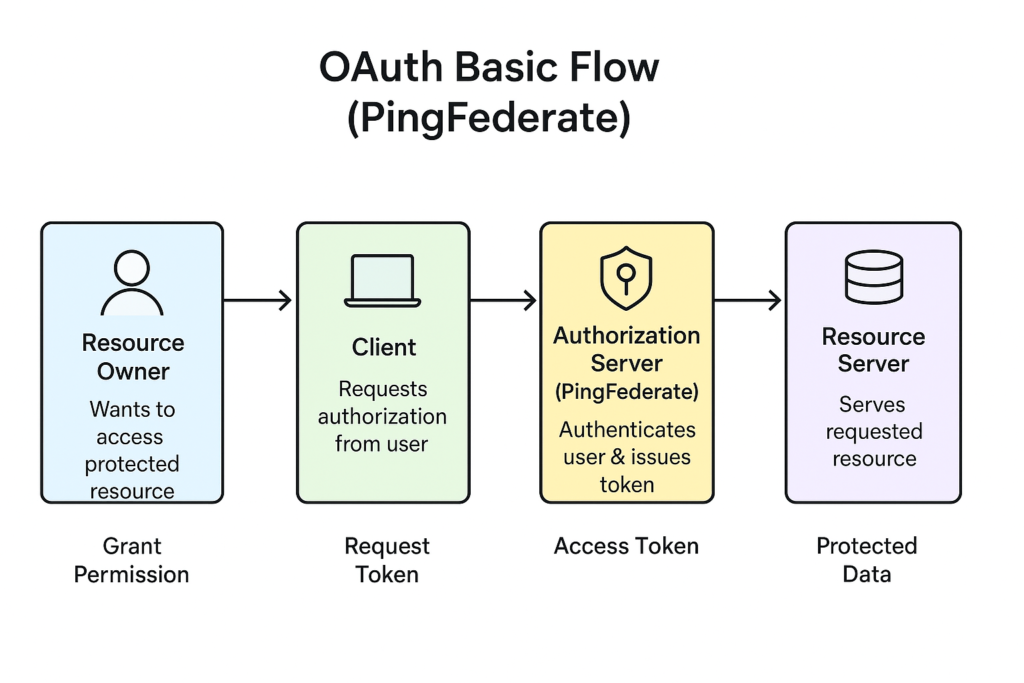
High-Level OAuth Flow in PingFederate
Here’s a simplified view of how it works:
- Client Requests Authorization – The application asks PingFederate for permission to access a resource.
- User Approves – The resource owner authenticates and authorizes access.
- PingFederate Issues Tokens – The Authorization Server provides an access token (and optionally a refresh token).
- Client Accesses Resource – The application uses the token to call the API (Resource Server).
- Token Validation – The Resource Server validates the token with PingFederate before granting access.
Why Choose PingFederate for OAuth
- Enterprise Security – Supports advanced security protocols and encryption.
- Flexibility – Works with different app types (native, web, API, SPA).
- Interoperability – Compatible with OpenID Connect and other identity standards.
- Scalability – Designed for large organizations with complex identity needs.
What’s Next
This article gives you the big-picture view of OAuth 2.0 with PingFederate.
In upcoming articles, we’ll cover:
- Components of OAuth 2.0 in PingFederate
- Understanding OAuth Grants: Types, Flows, and Applications
- Authorization Code Grant Flow in OAuth 2.0
- OAuth Implicit Flow in PingFederate
- Authorization Code with PKCE Flow | PingFederate
- Client Credentials Grant Type in OAuth 2.0
- Resource Owner Password Credentials (ROPC) Grant Flow in OAuth 2.0
- Refresh Tokens in PingFederate OAuth 2.0
- OAuth 2.0 Introspection Endpoint
- PingFederate OAuth 2.0 UserInfo Endpoint
- PingFederate OAuth 2.0 Token Revocation Endpoint
- Exploring OpenID Connect (OIDC) in PingFederate
- An Introduction to Identity and Access Management
- SP-Initiated SSO Flow
- Understanding the SAML Authentication Flow for IDP Initiated SSO
- Understanding the SAML SP-Initiated Single Logout (SLO) Flow
- LDAP Overview: Architecture, Terminologies, and Data Storage
- Adding an OAuth AC Client in PingFederate,getting endpoint token and authorization code token,json web token
- PKCE WITH OAUTH 2.0 IN PING FEDERATE
- Implicit Grant in PingFederate ,postman token and json web token
- (ROPC)Resource owner password credentials in ping federate,postman and json web tokens
- (OIDC)Open ID Connect in ping federate,obtaining postman token and json web token